Crypto Wallet Security arrives at the top of the headlines whenever a crypto wallet attack is exposed. Honestly, cyber attacks happen in all digitized industries. But have you ever considered why cryptocurrency wallet security is always the talk of town? Because crypto wallet developers keep rolling out security upgrades to meet the next level of protection. People see these upgrades as a solution to the existing issue. But in reality, those updates are shaping the future of crypto wallet protection.
Crypto Wallet Security is a set of protective measures to ensure complete protection of crypto assets and the wallet while managing crypto transactions. Now it is rising with many irresistible evolutions including Quantum Cryptography, MPC security, etc. But what makes sense here is, implementing robust security measures to defend against the threats. So as an investor, you should understand the security features your crypto wallet developer offers. Don’t worry! This blog will help you cover everything about cryptocurrency wallet security.
Before moving straight to the topic, let us first glance through the…
Potential Threats Against Crypto Wallet Security
Crypto wallet security will be in danger when any one of the following threats happens.
Phishing Attacks
Phishing attacks mean hackers create fake websites or applications similar to the original crypto wallet and steal wallet credentials from users. The credential includes private keys, secret keyphrases, and other login data. Phishing attacks are executed through messages/mail with vulnerable URLs, phone calls, etc.
Malware Attacks
Malware attacks are spreading malware to users’ devices like mobile, computer, etc, and stealing the wallet credentials. The malware monitors your wallet activities and steals sensitive information without your knowledge. Malware generally spreads through downloading files or software from unauthorized resources.
Physical Theft
Physical theft means directly stealing the hardware wallet from the user. The weakly configured hardware can compromise crypto wallet security easily and enable wallet access.
Social Engineering Attacks
A social engineering attack is manipulating users to reveal login credentials for wallet access. This type of attack happens through psychological manipulations like creating trust, a good impression, etc.
Attacks Through External Platforms
This type of attack is related to custodial wallets that are connected and managed by another platform. For instance, we can consider the custodial wallet of crypto exchanges. The cyber attack on the exchange platform also impacts the connected crypto wallets.
These are the potential threats necessitating the importance of investing in crypto wallet security. According to Cointelegraph’s report, more than $1 billion worth of crypto assets were stolen through 296 phishing incidents. Similarly, Coinpedia’s report confirms the total loss of $2.36 Billion through different crypto hacks that happened in 2024.
So implementing advanced security measures becomes important to safeguard the wallet from potential risks. A leading Crypto Wallet Development Service can help you implement the necessary components to protect against those security risks.
Essential Components of Cryptocurrency Wallet Security
Crypto Wallet Security is obtained through the combined working of its essential components. Here is an overview of them to improve your clarity.
Private Key Management
Private keys are made up of cryptographic algorithms to enable secure wallet access to users. In custodial wallets, private keys are stored in the wallet itself. And, non-custodial wallets let the users store the private key to offer complete control. Contrarily, MPC wallets have their own seed phrase verification process. Understand what your target audience expects and create a relevant wallet for your business.
Authentication Methods
Crypto wallet services are available through mobile, desktop, and browser extensions. Each of them follows different authentication methods to ensure crypto wallet security as mentioned below
- Device-based Password/PIN protection
- Two Factor/Multi-Factor Authentication (2FA/MFA)
- Biometric Authentication (Fingerprint, Face recognition, and Voice recognition)
- Multi-Signature Authentication
- Physical device verification (For hardware wallets)
The first three authentication methods are for secure wallet access. And, the last two are for approving crypto wallet transactions. You can combine any two or more of them as per your requirements.
Secure Wallet Communication
Secure wallet communication denotes how safely the data is transferred between the wallet, blockchain, and user. Wallet connection generally occurs through direct or APIs. But, the crypto wallet remains secure with higher-end encryption, TLS, and SSL cryptographic protocols. So there is minimal risk of hacking or data theft in the middle of communication.
Backup and Recovery Options
Backup and recovery options help users recover the wallet from potential losses like theft or hacking. The crypto wallet security binds with a 12 to 24-word keyphrase generated during wallet development. In case of loss, the user can recover the wallet access using this key phrase. This seed phrase is also known as a master key of cryptocurrency wallet security.
Storage Capacities
Based on the storage, crypto wallets can be classified as hot or cold wallets. Hot wallets (online) are directly connected to the internet where the chances of hacking are high. Cold wallet (offline) works offline and is connected to the internet when needed. So they are considered to be more secure than hot wallets. You can also prefer hot wallets with cold storage features.
These essential components ensure the crypto wallet security to fight against the potential threats. But for practical usage, both wallet users and service providers should observe certain guidelines to achieve maximum security.
How to Secure Your Crypto Wallet – Tips to Protect Your Assets
Here are the guidelines you should follow to ensure the crypto wallet security.
1. Protect Your Wallet With A Strong Password
- Always frame complex passwords with a combination of numbers, letters, and symbols.
- Have a unique password and avoid using the same password somewhere else.
- Use reliable password managers to protect your passwords.
2. Enable 2FA/MFA Authentication
- Along with password protection enable 2FA or MFA authentication to enhance the security.
- Set up SMS or e-mail-based authentication or connect with third-party authenticators like Google authenticator.
- For mobile crypto wallet security, you can enable biometric authentications.
3. Secure Your Private Keys With Cold Storage
- Use hardware wallets or cold storage to protect your private key and secret key phrases. This ensures secure access to keys and keeps them away from online threats.
4. Monitor Active Connections On Your Wallet
- Often check the active connections of crypto wallet and prevent connection with any decentralized applications not in use.
- Ensure the wallet is only enabled for required permissions.
5. Be Cautious In Handling Unknown Resources
- Don’t proceed with unknown links received through SMS or e-mail.
- Always download verified apps from authorized services to ensure crypto wallet security.
6. Stay Connected With Secure Internet
- Avoid connecting your wallet to public Wi-Fi or insecure VPNS.
- Always use private networks owned by you for secure wallet connectivity.
7. Backup The Crypto Wallet Regularly
- Backup your crypto wallet at least once a week and keep the backup in secure encrypted storage.
- Backups help in restoring the data when accidental data loss or hacking happens.
8. Keep Your Wallet Software Updated
- Always update your wallet to recent software provided by your crypto wallet developer.
- Enable auto-updates for mobile crypto wallet apps to ensure advanced cryptocurrency wallet security.
With these guidelines, your cryptocurrency wallet becomes secure and stays away from vulnerabilities. You may opt for crypto insurance as an extra layer of security. As technology grows, the future will bring more upgraded versions of crypto wallet security.
Future Innovations in Crypto Wallet Protection
The crypto wallet will receive consistent upgrades to enhance security and underlying technologies. They can stay protected and lead the market competition with innovative cryptocurrency wallet security. Here we have a glance at them.
Decentralized Identity Solutions
A decentralized identity solution can be effective in enabling crypto wallet access. This enables users to verify their wallet ownership by sharing the required information only. So the chances of phishing attacks and privacy risks will be less.
Web3 Security Standards
Web3-powered crypto wallets can support innovative features while providing enhanced connectivity and control to users. Their security standards are viable in secure dApp connectivity, interoperability of wallets, and secure communication. This strengthens your crypto wallet security to stay away from vulnerabilities.
Post-Quantum Cryptography (PCQ)
PCQ is better than the current cryptographic algorithm (RSA) in fighting against the threat of quantum computers. PCQ algorithms have complex mathematical structures that can not be solved by quantum computers. Thus it helps developers to create strong public and private keys to meet up with cryptocurrency wallet security.
Multi-Party Computation (MPC)
MPC technology splits private keys into seed phrases and enables wallet access when the seed phrases match perfectly. This Multi-party computation is already in practice for crypto wallet protection. Yet, the consistent upgrades in key management still make it considered a future innovation.
Threshold Signature Schemes (TSS)
TSS is nothing but a transaction approval scheme for crypto wallet security. Modern-day wallets follow multi-signature verification for transaction verification which is time-consuming. TSS signature helps developers to code a single signature that is compiled from multiple signatures.
These are the forefront innovations we can expect with cryptocurrency wallet security. However, an agile crypto wallet platform is essential to implement those innovations effectively. Coinsclone as a leading Crypto Wallet Development Company can help you create a wallet with top-notch security features. Want to explore how? Stay tuned for the upcoming section.
How Does Coinsclone Help You Achieve Crypto Wallet Security?
At Coinsclone, we first understand your requirements and prepare a roadmap to achieve your goals. Here is our working strategy that embraces cryptocurrency wallet security at every stage.
Understanding your Requirements
We gather your ideas first to understand your crypto wallet business ideology. Our experts clarify the requirements well and prepare a roadmap to achieve top-notch crypto wallet protection.
Determining the Type of Wallet
Once the ideology is clear, our team of specialists suggests the right type of wallet to meet your requirements. Based on that, the development process will be planned following the security protocols, asset storage, login methodologies, etc.
Defining Secure Key Management
This is the process of setting up the private key and secret phrase management. Private keys will be created and then encrypted with an Advanced Encryption Algorithm (AES256). Concurrently, the secret key phrase for backup and recovery will be created. The developer will determine the key management practices based on the wallet type.
Employing Robust Authentication
2FA and MFA are the ways to enable crypto wallet security during login. The authentication is processed through SMS, E-mail, or physical device verification. Additionally, we employ a multi-signature authorization to verify wallet transactions.
Following Secure Coding Practices
The process includes secure coding of wallet functionalities, verifying the code, and implementing an error-handling mechanism. We prefer authenticated programming languages for coding wallet functionalities and smart contracts. Under stringent measures, the codes will be verified for security and efficiency. This will keep your wallet away from software issues and cyber threats.
Integrating Modern Security Features
We prefer to stay on recent security features right from blockchain selection to implementing security features. Our crypto wallet solutions have browser detection security, anti-phishing protocols, malware mitigation, and key management servers as necessary security features. Further, we implement a Zero Knowledge Proof protocol to limit the data to third-party applications. You can add additional cryptocurrency wallet security measures as per your requirements.
Implementing Data Encryption and Storage
The wallet data including user credentials, wallet addresses, and transactions are encrypted by AES algorithms. So that the data can not be compromised without our relevant decryption algorithm. Speaking of storage, we prefer cold storage for private keys and asset storage. However, you can decide the type of storage for enhanced crypto wallet security.
Completing a Crypto Wallet Development
This is the final stage of crypto wallet development. The process includes the front-end and back-end development meeting the cryptocurrency wallet security. Our testing team will conduct thorough auditing on a smart contract and wallet functionality before deployment.
Ensuring Regulatory and Legal Norms
Our crypto wallet solutions adhere to the Global Data Protection Regulation (GDPR) and US Security and Exchange Commission (SEC) regulations. The customizable crypto wallet solution can add additional features to meet the operating country’s legal norms.
Conducting Periodical Security Auditing
The crypto wallet solutions come with necessary periodical security auditing and upgrading schedules. Based on your requirements, you can opt for real-time assessment programs to enhance the crypto wallet protection.
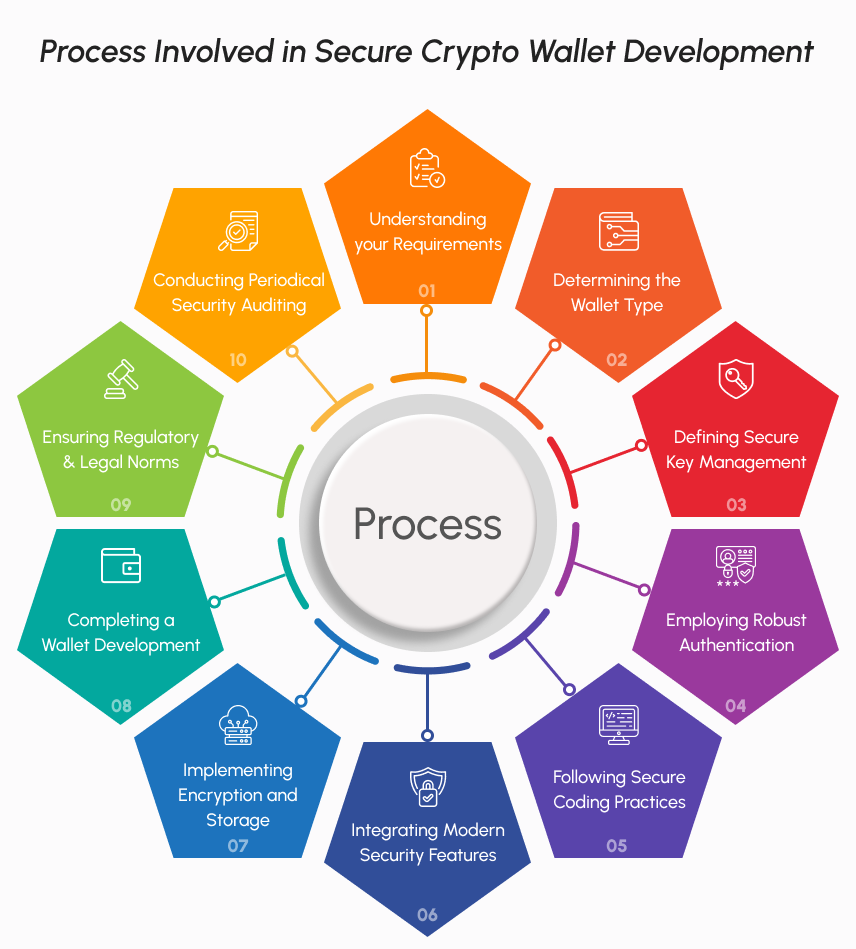
This is our streamlined crypto wallet development process prioritizing crypto wallet security. Based on the development method you choose, this process may have slight variations. You may choose our White Label Crypto Wallet Solution for creating a secure crypto wallet cost-effectively with your branding. However, we never compromise on cryptocurrency wallet security and quality at any stage. Apart from that, there are compelling reasons to choose us as your development partner.
Why Should You Choose Us for Secure Crypto Wallet Development?
Coinsclone is a leading Crypto Wallet Development Company that excels in creating security-first crypto wallets as per client requirements. We are a team of blockchain experts experienced in developing different blockchain applications and platforms. We follow secure coding practices and a streamlined development process assuring the remarkable quality of our products. Our crypto wallets are tamper-proof and designed to tackle real-world challenges in crypto wallet security and performance. This can help you build a crypto wallet business staying ahead of innovation with incredible profits. So why are you waiting? Get your free consultation right away
